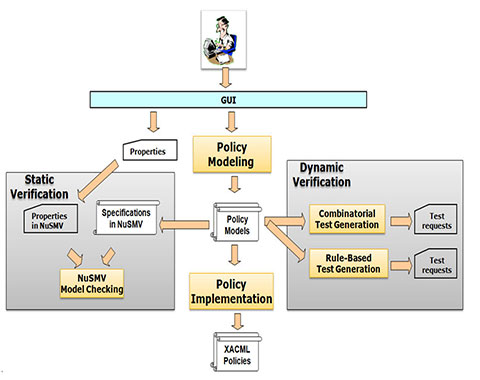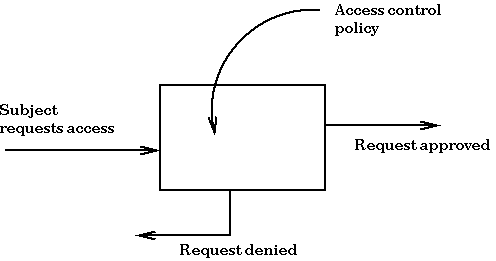
Access Control Methods Information Security Ppt Powerpoint Presentation Pictures Visual Aids Cpb | Presentation Graphics | Presentation PowerPoint Example | Slide Templates
Information Security Define Access Control Measures For Employees Ppt Icon Pictures PDF - PowerPoint Templates

Access Control: Don't Give Cybercriminals the Keys to your Business | 2020-03-05 | Security Magazine