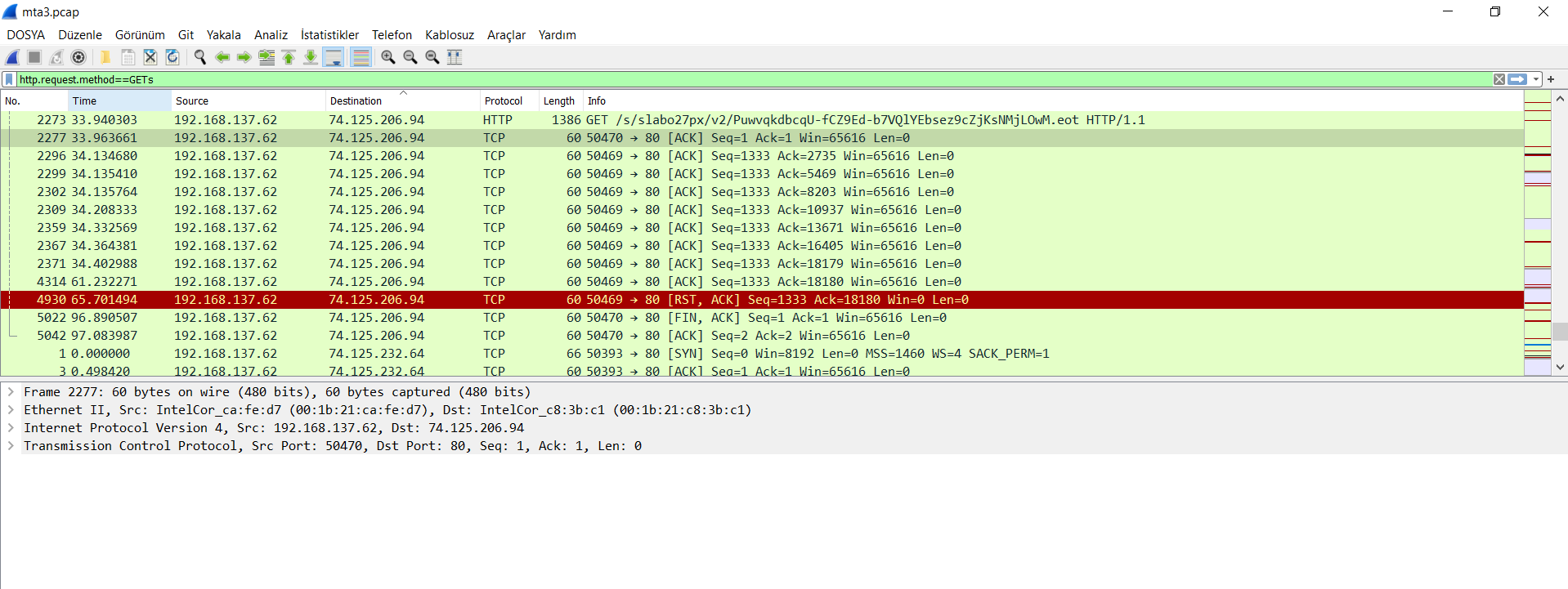
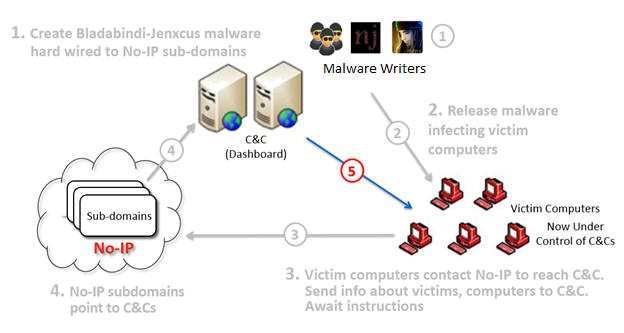
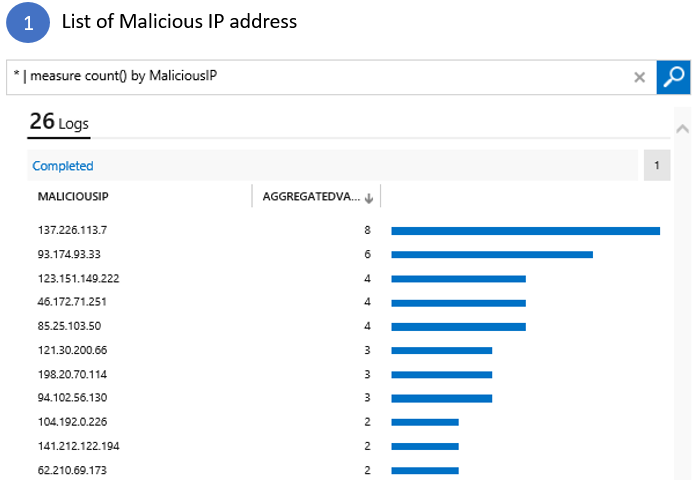
Find out if your servers are talking to a Malicious IP address with Operations Management Suite - Microsoft Community Hub

Intelligent Dynamic Malware Detection using Machine Learning in IP Reputation for Forensics Data Analytics - ScienceDirect

Any way to check/list the IP addresses in ThreatRadar - Malicious IP database | Imperva Cyber Community

IP and Host PC infected After successfully findingthe timestamp, IP,... | Download Scientific Diagram


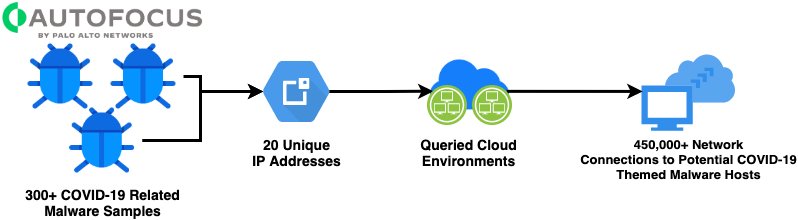


![5 Ways to Report an IP Address [2023 Guide] 5 Ways to Report an IP Address [2023 Guide]](https://whatsoftware.com/wp-content/uploads/2016/03/secureport-blocked-connections.png)